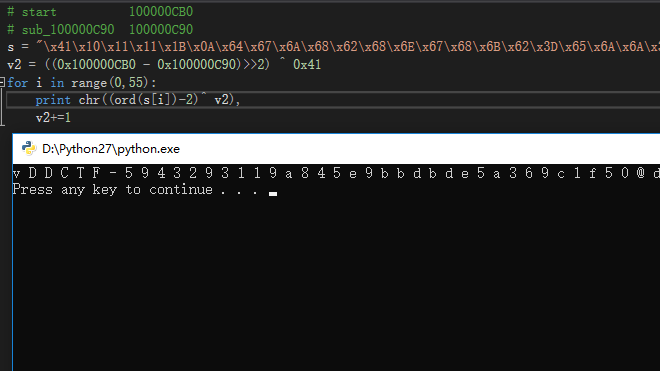
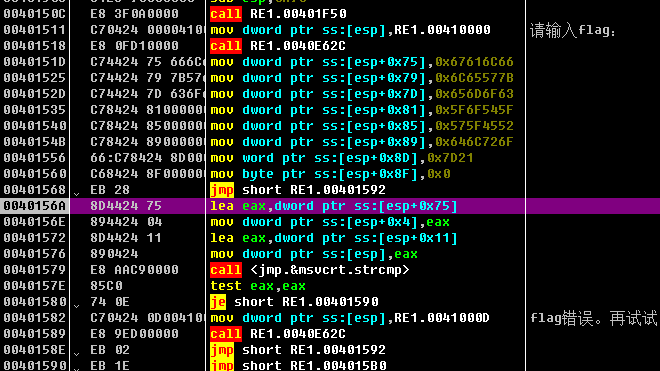
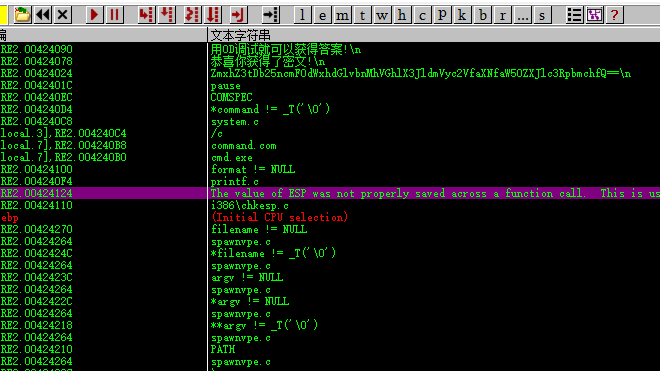
Web
EZwww
根据hint,发现源码泄露
1 | http://47.100.46.169:3901/www.zip |
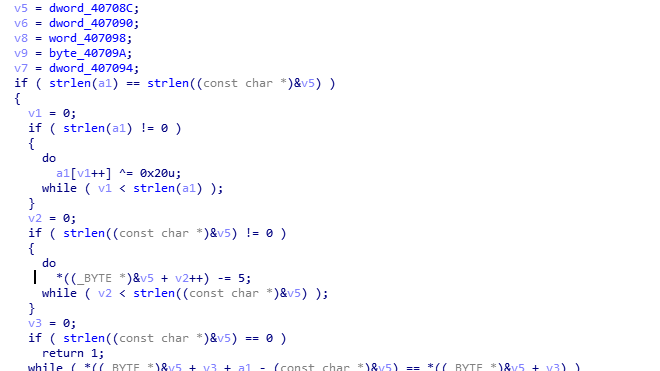
解压之后代码如下
1 | <html> |
发现只要以POST的形式a=base64_decode('c3ljbDB2ZXI=')成立,即可输出flag
Exploit如下
1 | import requests |
回显
1 | <html> |
SYC{Backup_1s_4_good_h4bit_l0l}
刘壮的黑页
一打开页面,全黑的,👴傻了
立即修改背景,给它洗白白
!(2.png)[2.png]
在底部发现php代码
1 | <?php |
在post发包时带着GET的参数即可
Exploit如下
1 | import requests |
Welcome
通过测试发现GET请求被ban了
尝试通过POST请求,发现可以得到页面源码,如下
1 | <?php |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 咲夜南梦's 博客!
评论