划水划到了第四名,期间学到了很多,但是队伍因时间可能无法参加线下赛了,着实可惜。
Crypto
0x1 Rsa
在线网站http://factordb.com/ 分解N
发现三个素数
然后查阅文档 三素数rsa算法
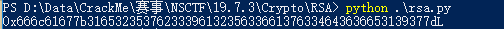
发现和两个素数差不多,然后上脚本,解出hex 转str
脚本如下:
1 | #coding:utf-8 |
转化为ascii即为flag
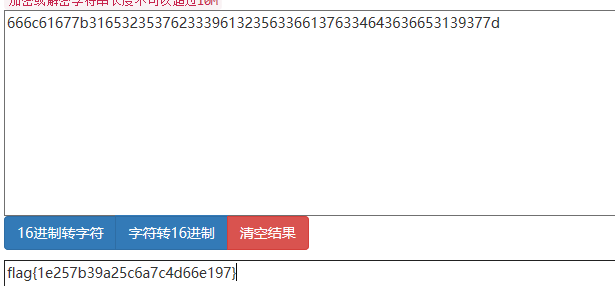
flag{1e257b39a25c6a7c4d66e197}
Misc
0x1
题目:
1 | a aa a a aa a a a a a a a a a aa a a a a a aa a aa a a a aaaa a a aa a aa a a aa a aa aa a a a a a aaa a aaa aa a a a aaaa a a a a a a a a a aa a a a a a a a aa a a aaa a aa aaaa a aaaa a a a aa a a aaa a a aa a a aa a a a aa a a a a aa a aa aaaa a aaaa a |
解法:
将a转为1空格转为0
然后直接转为十六进制
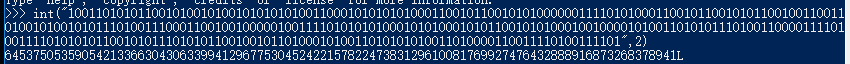
然后转化为ascii,然后进行栅栏得到MFTVYYTWJYVVU3TKLJHEUWS5FNWSY2LCPA======
1 | import base64 |
运行程序:flag{S0_so_SO_b0r1ng}
0x2
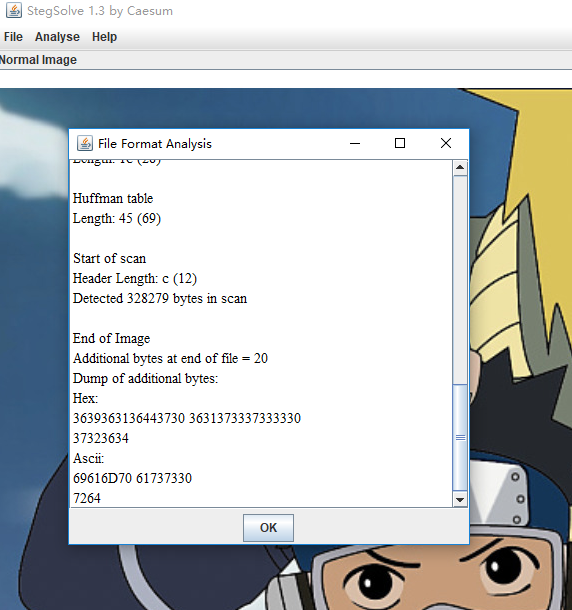
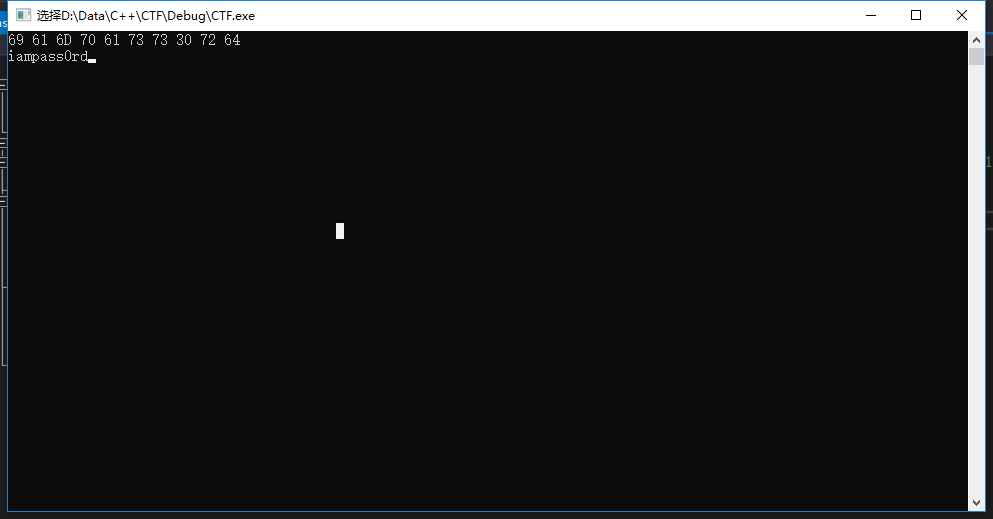
发现ascii解密后为iampass0rd
然后使用JPHS的seek,并输入上面的密码
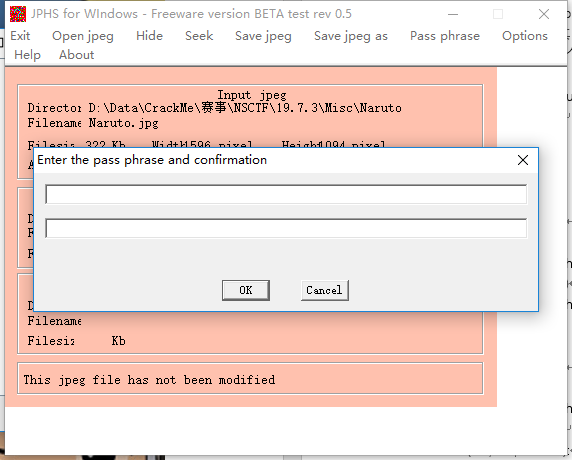
输入密码后,保存文件,然后打开看到flag
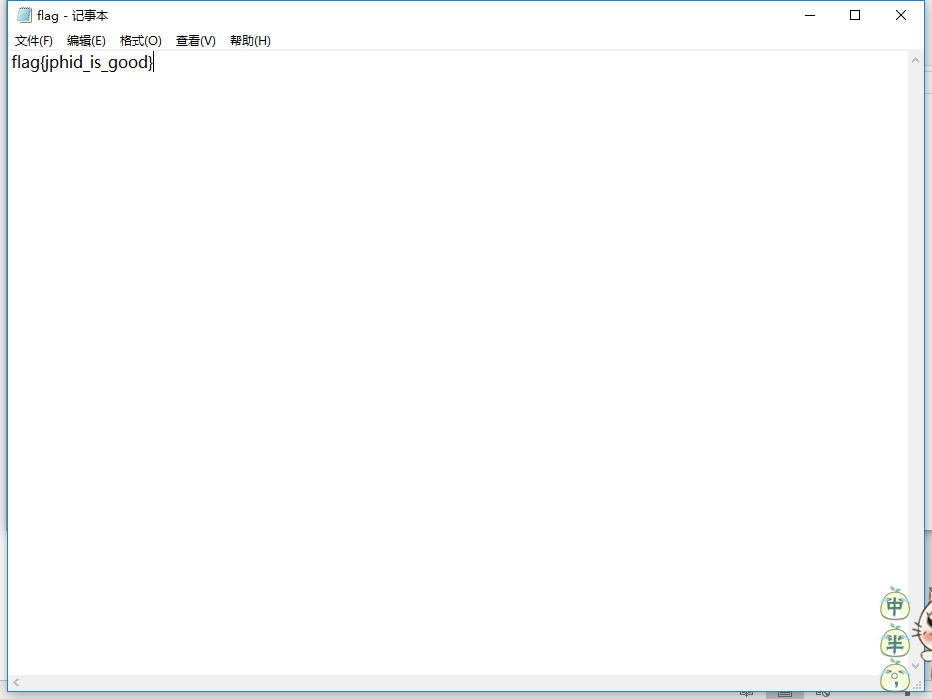
flag{jphid_is_good}
0x3
Log analysis
将所有带%的字符的数据全部转为对应的ascii
然后看到有sql注入,且flag格式为flag{xxxxxxxxxxxxxxxxx}
搜索’}’的ascii即125,然后看到!=,那么就向前搜索带!=的字符串,并且将!=后面的数字取出来
结果:49 102 108 97 103 123 51 50 56 55 102 101 51 48 48 102 50 56 101 50 52 97 101 102 97 50 100 56 54 56 56 51 56 51 50 99 57 102 125
然后写一个转化程序
1 | #define _CRT_SECURE_NO_WARNINGS |
然后输入49 102 108 97 103 123 51 50 56 55 102 101 51 48 48 102 50 56 101 50 52 97 101 102 97 50 100 56 54 56 56 51 56 51 50 99 57 102 125
即可拿到flag
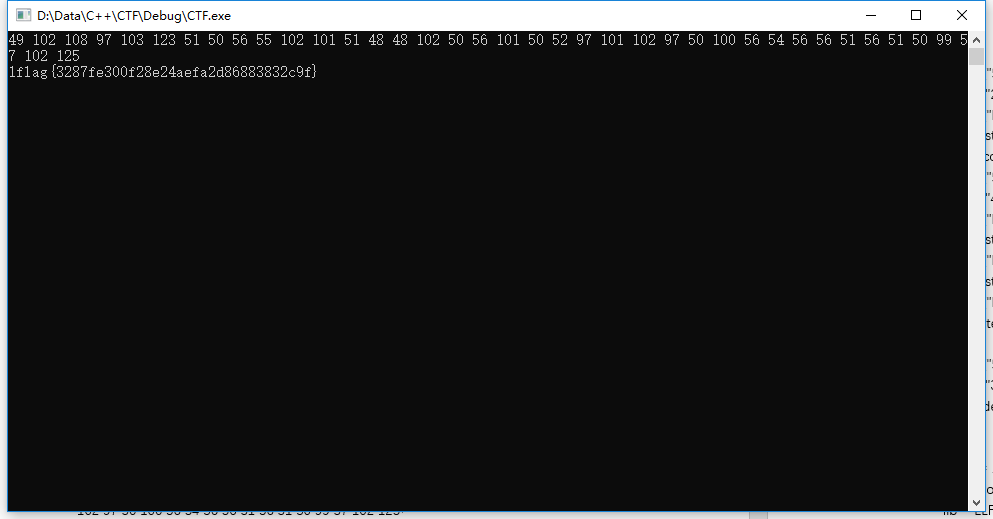
flag{3287fe300f28e24aefa2d86883832c9f}
Pwn
0x1
发现edit输入idx时没有检查存在数组越界的情况,可以越界到标准输出流stdout,然后修改里面的数据,实现libc溢出
得到libc之后,通过null by one将unsorted bin的pre_inuse修改掉,并配好prv_size将其free,前一个unsorted bin被free但我们chunk_list依旧存在该bin的指针,实现一定空间的任意写,然后我们在其中间之前申请的fastbin进行fastbin attack,申请到malloc_hook的错位位置即0x7f的前8个字节处
1 | from pwn import * |
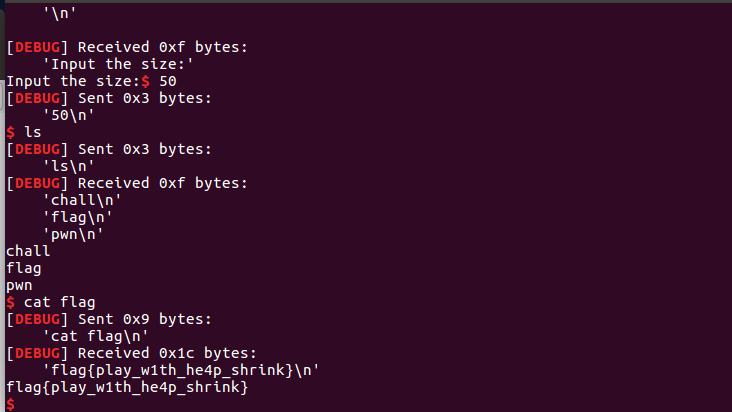
flag{play_w1th_he4p_shrink}
0x2
1、ida分析看到name处存在栈溢出,可以覆盖到chunk_list的低位数据,这里我们可以利用该漏洞实现堆内局部地址随意读写,利用unsorted bin free的时候会存在main_arena,然后通过修改name将指针调整到该处然后show即可leak libc
2、先使用fastbin attack覆盖malloc_hook为one_gadget发现全部失效。所以采用unsorted bin attack在free_hook低位地址写入7fxxxxxx数据,然后利用fastbin attack 申请堆块到0x000000000007f处,这样就可以覆盖free_hook,由于我们已经知道libc了,所以覆盖的数据为system地址,然后再字符的头部写入sh\x00,然后free掉这个chunk,就等效于执行了system(“sh”),至于为什么不用/bin/sh\x00,因为实际操作中,/sh这三个字符串被覆盖了,导致字符串残缺无法拿到shell。
3、因为使用了unsorted bin attack,所以破坏了堆块申请机制,只要申请非之前已经free的fastbin就会报错,这个问题我花了5个小时去调试,最后只需在unsorted bin attack之前申请然后free三种不同堆块,且保证unsorted bin attack过程中不会用到这些fastbin即可,在完成unsorted bin attack之后,只需还有能申请三个堆块,其中一块为0x68大小,且三个堆块的高位地址全部相同,就可以使用fastbin attack覆盖free_hook
1 | from pwn import * |
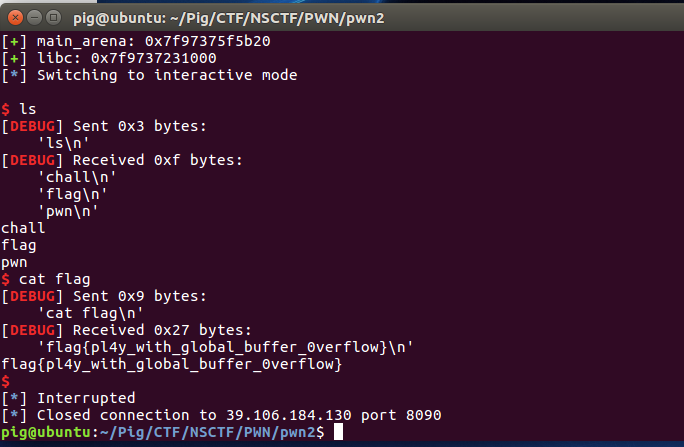
flag{pl4y_with_global_buffer_0verflow}
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 咲夜南梦's 博客!
评论